Burp Suite is an integrated platform for performing security testing of web applications. It is an integration of various tools put together for performing security testing of Web applications. Burp Suite is used to identify vulnerabilities and exploit them.
1.) Check your IP address by using ifconfig/ipconfig.
2.) Activate the interface you want to use in proxy options.
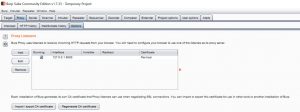
3.) Make sure the intercept is on.
4.) Set up the browser in the request-response process so that it is routed through port 8080 of your localhost in advanced network settings.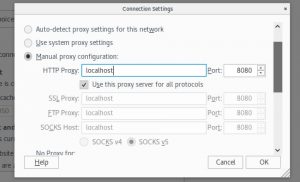
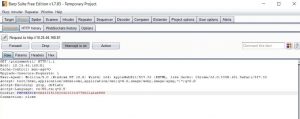
5.) Open any website that you want to find the vulnerabilities and the port number which you listened. Burp Suite will show information such as cookie, etc.
6.) The spider tool is used to get a complete list of URLs and parameters for each site. To run the spider on your Burp Suite, switch off your target interceptor.
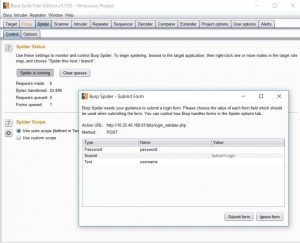
7.) The site map aggregates all of the information that Burp has gathered about applications.